Linux
Using Auditd to Monitor File Access in Linux: A Complete Guide
Imagine having complete visibility into every file accessed on your Linux system. Whether you’re a system administrator or a curious tech enthusiast, understanding who accesses which files and when can be crucial.
That’s where Auditd comes in. It’s like having a CCTV for your files, offering a detailed log of all file access activities. This tool not only enhances your system’s security but also gives you peace of mind. Are you ready to uncover the secrets of monitoring file access with precision and ease?
Dive into this guide to learn how Auditd can transform the way you manage your Linux environment, ensuring that nothing slips through the cracks.
What Is Auditd?
Linux users often find themselves in need of a reliable way to monitor file access and changes within their system. Whether you’re an IT professional or a hobbyist, understanding who is interacting with your files is crucial. This is where Auditd comes into play. But what exactly is Auditd?
Auditd is a powerful auditing tool native to Linux systems. It acts like a vigilant security camera, keeping an eye on file access and system events. With Auditd, you can track who accessed a file, when they did it, and what actions were performed.
Picture this: you’re managing a server with sensitive data. Suddenly, there’s a need to know who accessed a particular file. Auditd provides you with the logs that reveal every detail. It’s like having a personal detective in your system, ensuring transparency and accountability.
Setting up Auditd is straightforward, yet it offers a depth of detail that can be customized to fit your specific needs. Want to track changes in a particular directory? Auditd can do that. Curious about unauthorized access attempts? Auditd’s got your back.
How Does Auditd Work?
Auditd functions by maintaining a log of events. It listens to the kernel, capturing actions that match the rules you’ve defined. Think of it like setting up filters that catch only the events you care about.
When a file is accessed or modified, Auditd logs the event. This log includes user IDs, timestamps, and the nature of the action. You can then sift through these logs to pinpoint suspicious activity or confirm legitimate access.
Why Use Auditd?
Why would you need Auditd on your Linux system? Consider the peace of mind it provides. With Auditd, you have a robust tool that helps prevent data breaches and unauthorized access.
Imagine a scenario where data is compromised. Instead of scrambling to find the culprit, Auditd gives you a clear trail to follow. It’s not just about security; it’s about having control and clarity over your system’s activities.
Setting Up Auditd
Getting started with Auditd doesn’t require a degree in computer science. Begin by installing Auditd with a simple command. Once installed, you can start defining rules that suit your monitoring needs.
You’ll want to create rules that target specific files or directories. These rules tell Auditd what to watch for. As you refine your setup, Auditd becomes a tailored solution that fits seamlessly into your workflow.
Common Pitfalls And Solutions
While Auditd is robust, it’s not without its quirks. Some users find themselves overwhelmed by the sheer volume of logs. It’s crucial to define precise rules to avoid unnecessary data.
Consider using tools that help filter and manage these logs. Regularly review your rules and logs to ensure they align with your objectives. Remember, your setup should evolve with your needs.
Have you ever found yourself questioning who accessed a file on your Linux system? Auditd could be the answer you’re seeking. With its detailed logs and customizable rules, it offers a layer of security that’s both comprehensive and user-friendly.
Have you tried Auditd yet? What challenges did you face? Share your experiences and insights in the comments below. Your journey could help others navigate the complexities of file monitoring in Linux.

Credit: medium.com
Benefits Of File Monitoring
Auditd helps monitor file access in Linux, enhancing security by tracking changes and unauthorized access. This tool provides detailed logs, allowing quick detection of suspicious activities, thus protecting sensitive data effectively.
Monitoring file access in Linux using Auditd offers numerous benefits that can significantly enhance your system’s security and integrity. By keeping a close watch on file access, you can detect unauthorized activities, ensure compliance, and maintain system performance. Whether you’re managing a personal server or overseeing a corporate infrastructure, understanding these benefits can help you safeguard your data effectively.Enhanced Security
File monitoring is like setting up a vigilant guard over your data. It alerts you to suspicious activities, helping you respond promptly to potential threats. Imagine receiving a notification the moment a sensitive file is accessed by an unauthorized user. This proactive approach can prevent data breaches and protect your sensitive information.Compliance Assurance
Many industries have strict compliance requirements regarding data handling and protection. Auditd helps you stay compliant by providing detailed logs of file access. These logs can serve as proof during audits, demonstrating that you have a robust system in place to monitor and protect data access.Performance Optimization
Have you ever noticed a system slowdown and wondered what caused it? File access monitoring can help you identify files that are frequently accessed, allowing you to optimize system resources accordingly. By understanding access patterns, you can make informed decisions about resource allocation and system improvements.Data Integrity
Ensuring that your data remains unchanged and trustworthy is crucial. With file monitoring, you can track changes to critical files and quickly revert unauthorized modifications. This capability is invaluable in maintaining the integrity of your data, especially in environments where data consistency is key.Improved Accountability
File access logs create a clear trail of who accessed which files and when. This transparency fosters accountability among users and can deter malicious actions. Knowing that every access is recorded encourages responsible behavior, reducing the likelihood of intentional data tampering. Have you considered how file monitoring might transform your approach to security and compliance? By leveraging these benefits, you can create a safer and more efficient environment for your data.Installing Auditd
Auditd efficiently monitors file access on Linux systems. It tracks changes, accesses, and modifications to ensure security. Simple installation enhances system monitoring capabilities.
Installing Auditd on your Linux system is the first step towards securing and monitoring file access. It’s like adding a vigilant security guard who tirelessly watches over your files. Once installed, Auditd provides detailed records of all file access events, helping you keep your system safe and sound. It’s straightforward, but you need to follow the right steps to ensure it works effectively. Let’s dive into how you can get Auditd up and running. ###Step 1: Update Your Package List
Begin by updating your package list to ensure you have the latest information. Open your terminal and type: “`bash sudo apt update “` This command refreshes the list of available packages. It helps your system know where to find the latest version of Auditd. ###Step 2: Install Auditd
With your package list updated, it’s time to install Auditd. Type the following command in your terminal: “`bash sudo apt install auditd “` This command installs Auditd along with the necessary tools. It’s usually a quick process, and you’ll be ready for the next step in minutes. ###Step 3: Verify The Installation
After installation, you should verify that Auditd is correctly installed. You can do this by checking its status: “`bash sudo systemctl status auditd “` If you see a message indicating Auditd is active and running, congratulations—you’ve installed it correctly. ###Step 4: Enable Auditd To Start At Boot
To ensure Auditd starts automatically whenever your system boots, enable it with: “`bash sudo systemctl enable auditd “` This step ensures your file monitoring starts without any manual intervention. It’s like having a guard who never sleeps. ###Step 5: Configure Auditd Rules
Now, it’s time to set up rules for monitoring specific files or directories. You can add rules by editing the audit rules file: “`bash sudo nano /etc/audit/rules.d/audit.rules “` Add lines specifying which files or directories you want to monitor. For example, to monitor changes to the `/etc/passwd` file, add: “`bash -w /etc/passwd -p wa -k passwd_changes “` Here, `-w` specifies the file, `-p wa` sets the permissions to watch (write and attribute changes), and `-k` assigns a key for easy searching. ###Step 6: Restart Auditd Service
After configuring your rules, restart the Auditd service to apply changes: “`bash sudo systemctl restart auditd “` Restarting ensures your new rules take effect immediately. It’s a simple way to activate your customized monitoring setup. ###Step 7: Test Your Setup
Finally, test your configuration by accessing a monitored file. Then, check the audit logs with: “`bash sudo ausearch -f /etc/passwd “` You should see log entries related to the file access. This confirms your setup is working. Installing Auditd is a foundational step in securing your Linux system. Each step you take strengthens your system’s defenses. Have you set up Auditd on your system yet? If not, now’s the perfect time to start.Configuring Auditd
Auditd helps track who accesses files in Linux. Configure rules to watch specific files and directories. Alerts provide insights into unauthorized access attempts, ensuring data security.
Configuring Auditd is crucial for monitoring file access in Linux. It helps track unauthorized changes and ensures system security. Auditd, a comprehensive auditing tool, logs significant system events. This blog section guides you through configuring Auditd effectively. Follow these steps to enhance your system’s security.Setting Up Audit Rules
Begin by installing Auditd on your Linux system. Use your package manager to do this. Once installed, enable the Auditd service. Use the command `systemctl enable auditd` for this. Start the service using `systemctl start auditd`. Your system is now ready to set audit rules. Define audit rules based on your needs. These rules tell Auditd what to monitor. They help in tracking specific files or directories. Edit the `/etc/audit/rules.d/audit.rules` file to add rules. After adding rules, restart the Auditd service. This applies the new settings.Understanding Audit Rules Syntax
Audit rules have a specific syntax. It includes parameters like `-w`, `-p`, `-k`. The `-w` flag specifies the path to watch. The `-p` flag indicates the permissions to monitor. Use `r` for read, `w` for write, `x` for execute, and `a` for attribute changes. The `-k` flag assigns a key to the rule. This helps in filtering logs. For example, to monitor file reads, use `-w /path/to/file -p r -k read_access`. This rule logs every read access to the specified file. Understanding this syntax ensures precise monitoring.Monitoring File Access
Monitoring file access in Linux is crucial for security and compliance. Auditd is a powerful tool that helps track who accesses files and when. With Auditd, you can easily set up rules to monitor specific files or directories. This tool provides detailed insights into file access patterns, enabling system administrators to secure sensitive data efficiently.
Creating File Access Rules
Start by configuring Auditd to monitor file access. Define rules that specify which files or directories you want to track. Use the command line to set these rules. This process helps create a secure environment. Tailor the rules to meet your organization’s needs. Aim for a balance between security and performance.
Tracking Specific Files Or Directories
Focus on tracking files that contain sensitive information. Use Auditd to monitor these files regularly. Set up alerts for unauthorized access attempts. This proactive approach helps prevent data breaches. Monitor directories that hold critical system files. Keep track of changes to these files for enhanced security.
Analyzing Audit Logs
Analyzing audit logs is crucial for understanding file access activities in Linux systems. These logs provide insights into who accessed files and when. This information helps in identifying unauthorized access and maintaining security. Knowing how to analyze logs efficiently can enhance your system’s security posture.
Viewing Logs With Aureport
Aureport simplifies viewing audit logs. It generates reports from audit logs. Use it to display recent file access events. Run the command aureport -f in the terminal. It provides a summary of file access activities. This helps in quickly reviewing recent actions.
Interpreting Log Entries
Interpreting log entries requires understanding key fields. Each entry includes a timestamp, user ID, and file path. The timestamp shows when the file was accessed. The user ID reveals who accessed it. The file path indicates the file involved. Look for patterns or unusual access times. This can highlight potential security issues.
Troubleshooting Common Issues
Using Auditd to monitor file access in Linux can enhance system security. Yet, it’s not always smooth sailing. Users often encounter issues that can disrupt its functionality. Identifying these issues can save time and prevent frustration. This section will guide you through common problems and their solutions.
Configuration File Errors
Incorrect configuration files are a frequent issue. Check for syntax errors in the /etc/audit/auditd.conf file. Ensure all paths and permissions are correct. Small mistakes can cause big problems.
Insufficient Permissions
Lack of permissions can prevent Auditd from working. Ensure that the Auditd service has proper access rights. Verify that it can read and write to necessary directories.
Auditd Not Starting
Sometimes, the Auditd service fails to start. Check the system logs for error messages. Use systemctl status auditd to diagnose the issue. Restart the service with correct configurations.
Logs Not Generated
Missing logs can confuse users. Ensure that the audit rules are correctly set. Use auditctl -l to list current rules. Adjust them to match your monitoring needs.
Performance Issues
High system load can affect Auditd’s performance. Review the number and complexity of audit rules. Simplify rules to reduce system strain. Regularly monitor the system’s performance metrics.
Excessive Log Files
Auditd can generate large log files quickly. This can fill up disk space. Set up log rotation to manage file size. Configure /etc/logrotate.d/audit for efficient log management.
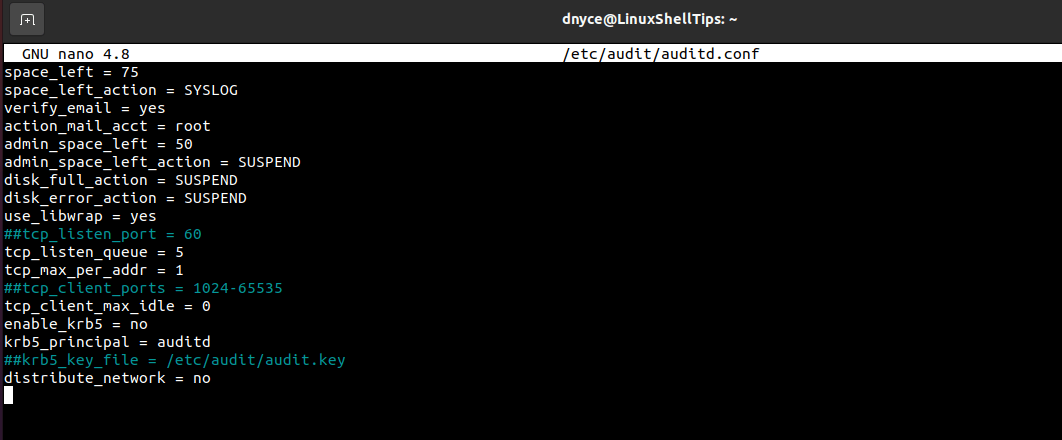
Credit: www.ubuntumint.com
Best Practices For Auditd
Monitoring file access in Linux is crucial for maintaining system security, and Auditd is a powerful tool for this task. To make the most out of Auditd, it’s essential to follow best practices that enhance efficiency and reliability. Whether you’re a system administrator or a security enthusiast, understanding these practices can significantly bolster your monitoring capabilities.
Ensure Proper Configuration
Auditd requires careful configuration to function optimally. Start by defining what files and directories you need to monitor. This prevents unnecessary logging and keeps your system’s performance intact. For instance, monitoring critical directories like /etc or user home directories can be a good start.
To configure Auditd, you should edit the audit rules file, usually located at /etc/audit/audit.rules. Make sure you specify file paths and permissions accurately to capture relevant events.
Utilize Auditd Filters
Filters are indispensable for narrowing down the vast amount of data Auditd can generate. By setting up filters, you can focus on specific types of file access, such as read, write, or execute actions. This helps in pinpointing suspicious activities without being overwhelmed by data.
For example, if you only want to track write access to a file, you can set a rule like: auditctl -a always,exit -F dir=/path/to/directory -F perm=w. This ensures you’re alerted whenever a file write occurs.
Regularly Review Audit Logs
It’s easy to set up Auditd and forget about it, but regular log reviews are vital. Set a schedule to go through the logs and look for unusual patterns or entries. This proactive approach can help you catch potential security breaches early.
Consider using tools like ausearch and auditctl for efficient log analysis. They offer powerful querying capabilities to help you sift through the logs quickly.
Implement Log Rotation
Audit logs can grow large and unwieldy over time, impacting system performance. Implementing log rotation ensures that older logs are archived, keeping your system responsive. Use tools like logrotate to automate this process.
Log rotation not only saves disk space but also helps in organizing logs for easier access and review. It’s a small step that makes a big difference in maintaining system health.
Secure Auditd Configuration Files
Your Auditd configuration files are as critical as the logs themselves. Ensure these files are secure and accessible only by authorized personnel. This prevents tampering and ensures the integrity of your monitoring setup.
Set proper file permissions and consider using tools like SELinux or AppArmor for added security. These measures protect your configuration from unauthorized changes.
Are you taking these steps to maximize Auditd’s potential? The effectiveness of your file monitoring depends heavily on how well you implement these practices.
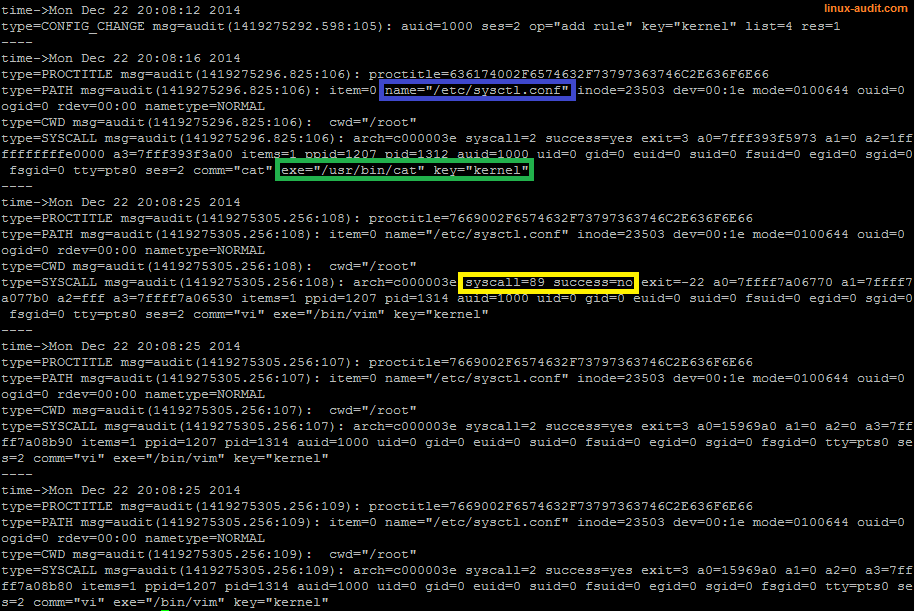
Credit: linux-audit.com
Frequently Asked Questions
How To Check File Access In Linux?
Use the `ls -l` command to check file access permissions in Linux. It displays details like owner, group, and permission settings. The permissions are shown in the format (rwx) for read, write, and execute. Understanding these details helps in managing file access efficiently.
How Can You Track Changes To System Files Using Auditd?
Install AuditD and configure audit rules to monitor system files. Use the command `auditctl` to set rules. Specify file paths to track. Review logs using `ausearch` or `aureport` to see file access and modifications. This helps in detecting unauthorized changes and ensuring system security.
How Do I Monitor Open Files In Linux?
Use the `lsof` command to monitor open files in Linux. It lists all open files and processes. You can filter results using options like `-u` for specific users or `-p` for specific processes. This tool helps track file usage efficiently.
How To Monitor File Access?
Use file monitoring tools like SolarWinds, Nagios, or Windows Event Viewer. They track and log file access activities effectively. Configure alerts for unauthorized access attempts. Regularly review logs to ensure data security. This proactive approach helps safeguard sensitive information and maintain compliance.
Conclusion
Auditd empowers Linux users with effective file access monitoring. It enhances security by tracking file activities. With simple commands, you configure Auditd to suit your needs. Regular monitoring helps identify suspicious actions early. This tool aids in maintaining system integrity.
It supports compliance with security protocols. Easy setup ensures even beginners can use it. Clear logs provide valuable insights. Auditd is a vital asset for anyone concerned with Linux security. Start monitoring today to protect your files and data. Keep your system secure and efficient with Auditd.
-

 DevOps6 years ago
DevOps6 years agoSaltstack Tutorial for beginners [2025]
-

 DevOps6 years ago
DevOps6 years agoHow to build a Docker cron job Container easily [2025]
-

 Linux7 years ago
Linux7 years agomail Command in Linux/Unix with 10+ Examples [2025]
-

 DevOps6 years ago
DevOps6 years agoDocker ADD vs COPY vs VOLUME – [2025]
-
 DevOps6 years ago
DevOps6 years agoHow to setup Pritunl VPN on AWS to Access Servers
-

 Linux7 years ago
Linux7 years agoGrep Command In Unix/Linux with 25+ Examples [2025]
-

 Linux7 years ago
Linux7 years agoFind command in Unix/Linux with 30+ Examples [2025]
-
Linux6 years ago
How To setup Django with Postgres, Nginx, and Gunicorn on Ubuntu 20.04

