DevOps
How to Set Up a Chroot Jail in Linux: Step-by-Step Guide
Are you concerned about the security of your Linux environment? Setting up a chroot jail might be the solution you need.
Imagine having a secure bubble where you can run applications without worrying about them affecting the rest of your system. It’s like creating a virtual sandbox that keeps potential threats at bay, ensuring that your core system remains safe and sound.

You don’t have to be a tech guru to achieve this. With a few straightforward steps, you can enhance your system’s security and gain peace of mind. Dive into this guide to discover how you can easily set up a chroot jail in Linux and protect your digital world.

Credit: www.geeksforgeeks.org
What Is A Chroot Jail?
Understanding the concept of a Chroot Jail is crucial for Linux security. A Chroot Jail is a method to isolate programs within a confined directory. This limits the access of programs to the system files. It enhances security by restricting unauthorized access to sensitive parts of the system.
A Chroot Jail modifies the root directory for a specific process. The process can only access files within its new root directory. This isolated environment helps in testing and development. It prevents harmful programs from affecting the entire system.
Why Use A Chroot Jail?
Using a Chroot Jail minimizes risks to the main system. It provides a sandbox for testing software. Developers can safely run applications without system-wide risks. This approach is essential for maintaining system integrity.
How Does A Chroot Jail Work?
A Chroot Jail creates a virtual environment by changing the root directory. It confines a program to a designated directory. The program operates within this restricted space. This reduces the threat of accessing critical files.
Benefits Of A Chroot Jail
Chroot Jails enhance security by limiting file access. They allow safe testing of new applications. Users can isolate applications from the main system. This prevents potential harm from untrusted software.
Benefits Of Using Chroot Jail
Setting up a Chroot Jail in Linux offers numerous benefits. It enhances security by creating isolated environments. This technique is invaluable for administrators and developers. Let’s explore the advantages of using Chroot Jail.
1. Enhanced Security
Chroot Jail creates a separate space for applications. This isolation limits access to the rest of the system. It prevents unauthorized users from reaching critical files. Security breaches become less likely. It is a simple yet powerful tool for safeguarding data.
2. Controlled Environment
It provides a controlled environment for testing. Developers can safely experiment with new applications. Any mistakes remain confined within the Chroot Jail. This isolation ensures the main system stays unaffected. It is ideal for trying out new software or updates.
3. Flexibility
Chroot Jail offers flexibility in managing applications. Administrators can run different versions of software. Each version operates in its own isolated space. This flexibility aids in testing compatibility. It is beneficial for systems requiring varied configurations.
4. Resource Management
It helps in efficient resource management. Administrators can allocate specific resources to each jail. This allocation prevents resource hogging by applications. It ensures balanced system performance. Resource control becomes easier and more effective.
5. Simplified Maintenance
Maintenance tasks become simpler with Chroot Jail. Administrators can update or modify applications within the jail. These changes do not impact the main system. It streamlines the process of managing software. Maintenance becomes less daunting and more organized.
Preparing Your System
Setting up a chroot jail in Linux starts with system preparation. This process ensures a secure environment for your applications. Preparing your system involves verifying requirements and installing necessary tools. Each step contributes to a successful chroot jail setup.
Checking System Requirements
Ensure your system meets basic requirements. Verify your Linux distribution version. Ensure it’s compatible with chroot jail configurations. Check available storage space. You need sufficient space for the chroot environment. Check user permissions. Administrative privileges are necessary for setup. Confirm network configurations. Stable connectivity is essential for tool installations.
Installing Necessary Tools
Start by installing essential tools. Package managers simplify installations. Use apt-get or yum for efficient software management. Ensure you have basic utilities. Install tools like tar and wget. These assist in managing files and fetching packages. Consider installing security tools. Tools like SELinux enhance security within the chroot jail. Set up monitoring tools. They provide insights into resource usage and system performance.
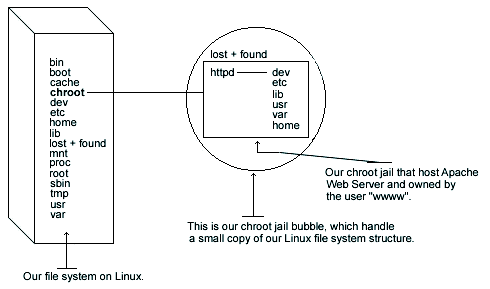
Credit: tldp.org
Creating The Chroot Environment
Creating a chroot environment in Linux is crucial for system security. It isolates programs from the rest of the operating system. This helps in preventing malicious software from affecting other parts. To start, you’ll need to set up a dedicated environment. This involves creating directories and copying necessary files.
Setting Up Directory Structure
Begin by creating a new directory. This will serve as the root for the chroot environment. Use the command mkdir -p /path/to/chroot. This command ensures the path is created if it doesn’t exist. Organize the directory with essential folders. Common folders include bin, lib, and etc. These directories will hold necessary files and configurations.
Copying Essential Files
Copy essential files into the chroot directory. Start with the necessary binaries. Use commands like cp /bin/bash /path/to/chroot/bin/. Ensure these files have the right permissions. Next, copy library files. Use the ldd command to find dependencies. For example, ldd /bin/bash lists required libraries. Copy each library file into the lib directory.
Copy essential configuration files too. Place them in the etc folder. Files like passwd and group are important. They help manage user permissions within the chroot environment.
Configuring The Chroot Jail
Setting up a Chroot Jail in Linux involves isolating processes to enhance security. This technique helps prevent unauthorized access by restricting user activities within a specified directory. Proper configuration ensures that any potential vulnerabilities are contained, safeguarding the system effectively.
Setting up a chroot jail in Linux can significantly enhance your system’s security by isolating applications from the rest of your operating system. Once you’ve created the chroot environment, the next crucial step is configuring it correctly. This involves setting permissions and defining user access to ensure your chroot jail is secure and functional. Let’s dive into the specifics of configuring your chroot jail effectively.
###
Adjusting File Permissions
Permissions are the gatekeepers of your chroot jail. They determine who can access, modify, or execute files within the environment. Ensure that only the necessary files have execute permissions to reduce potential security risks.
Consider this: when I first set up a chroot jail, I overlooked file permissions. It resulted in unexpected access issues that took hours to resolve. Learn from my mistake and check permissions meticulously.
Use commands like chmod to adjust these permissions. For instance, setting a file to 755 allows the owner full control while giving others read and execute access. This level of detail can prevent unauthorized changes while maintaining functionality.
###
Setting Up User Accounts
User accounts in a chroot jail define who can enter the jail and what they can do once inside. Create specific user accounts for your chroot environment rather than using existing system accounts. This ensures that users have only the necessary permissions without access to the broader system.
Think about the users who need access. Do they need admin privileges, or can they operate as standard users? Tailor user roles to their specific needs to maintain a secure environment.
Create user accounts using the useradd command. Assign them a shell like /bin/bash, but remember to copy necessary binaries to the chroot jail. This step is crucial to ensure they can execute commands within the jail without issues.
Configuring your chroot jail effectively can be straightforward if you pay attention to these details. Have you ever considered the impact of a misconfigured chroot environment? Taking the time to adjust permissions and set up user accounts can save you from potential headaches down the road.

Credit: linuxize.com
Testing The Chroot Jail
Testing the Chroot Jail is a critical step. It ensures your setup functions as intended. A successful test verifies your system’s security and isolation. Let’s explore key areas to focus on during testing. This includes verifying the setup and troubleshooting issues.
Verifying The Setup
First, confirm the chroot jail environment. Use the chroot command to enter the jail. Check if the environment is isolated. Try running basic commands like ls or pwd. They should execute without errors.
Next, verify the presence of essential files. Use the ls command. Ensure necessary binaries like bash and ls are accessible. Missing files can cause functionality issues.
Check the permissions on directories and files. Incorrect permissions might lead to security risks. Use ls -l to review file permissions inside the jail.
Troubleshooting Common Issues
Encountering issues? Start by checking error messages. They often reveal the problem. If commands fail, check if necessary binaries exist in the jail.
Another common issue is missing libraries. Use the ldd command to list required libraries. Ensure all listed libraries are inside the jail.
Check for permission errors. Permissions might restrict access to files. Use chmod to adjust permissions if necessary.
Verify the environment variable settings. Incorrect settings can lead to unexpected behavior. Adjust them to match the host system if needed.
Networking issues may arise. If relevant, ensure network configurations are correct. Use commands like ping to test network connectivity within the jail.
Testing the chroot jail thoroughly ensures a secure and functional setup. Regular checks prevent potential issues and maintain system integrity.
Maintaining The Chroot Jail
Setting up a chroot jail in Linux enhances system security by isolating processes. This controlled environment limits access to resources, ensuring sensitive data stays protected. Regular maintenance and monitoring are crucial for its effectiveness and stability.
Maintaining the integrity of your chroot jail in Linux is crucial for ensuring its security and functionality. Once you’ve set up your chroot environment, it doesn’t end there. Consistent maintenance is key to preventing vulnerabilities and keeping your system safe. It’s like tending to a garden; regular upkeep ensures everything runs smoothly and securely. Let’s delve into some practical steps for maintaining your chroot jail.
###
Updating Software
Keeping the software within your chroot jail updated is essential. Outdated software can be a gateway for security vulnerabilities. Ensure you regularly update the packages within the chroot environment.
You might find it helpful to schedule routine checks for updates. This proactive approach can prevent potential issues before they arise. Wouldn’t it be better to spend a few minutes on updates than hours on fixing problems?
Consider using package managers like apt or yum inside your chroot jail. They simplify the update process significantly. Just a few commands, and your software stays current and secure.
###
Monitoring Security
Security monitoring is another critical aspect of maintaining your chroot jail. Regularly check for any unauthorized access or unusual activity. It’s like keeping an eye on your house when you’re away.
Implement logging mechanisms within the chroot jail. They can provide insights into user activities and system changes. Logs can be invaluable in identifying potential breaches or misconfigurations.
Periodically review these logs and look for patterns or anomalies. This habit can help you catch potential threats early. Do you have a routine for reviewing logs, or is it time to start one?
Using security tools tailored for Linux can also bolster your monitoring efforts. Tools like chkrootkit or rkhunter can help detect rootkits and other malicious software. These tools add an extra layer of security, giving you peace of mind.
By focusing on updating software and monitoring security, you ensure that your chroot jail remains a secure and stable environment. Remember, consistent maintenance is the backbone of a robust chroot jail. What steps will you take today to safeguard your system?
Use Cases For Chroot Jail
Setting up a Chroot Jail in Linux enhances security by isolating applications from the main system. It restricts programs, preventing them from accessing unauthorized resources. This method is vital for running potentially vulnerable services safely.
Setting up a chroot jail in Linux can be a powerful way to enhance security and manage user access. But why would you want to use a chroot jail? There are several practical applications that can make your system more secure and efficient. Let’s dive into some common scenarios where chroot jails shine.
Web Server Isolation
Running multiple websites on a single server can be risky. If one site gets compromised, others are at risk too. By using chroot jails, you can isolate each web service. This means if one service is hacked, the others remain untouched.
Testing And Development
Developers often need a safe space to test their code. A chroot jail provides a controlled environment where you can run tests without affecting the rest of the system. It’s like having a mini-lab on your machine. Have you ever worried about a test going rogue and crashing your entire system?
Restricting User Access
Sometimes you need to give users limited access to certain system resources. Chroot jails can restrict users to a specific directory, preventing them from accessing sensitive data. This is especially useful for shared servers where privacy is a concern. Imagine being able to confidently allow guest access without fretting over data leaks.
Building Packages
When compiling packages, you want to ensure they won’t interfere with existing software. A chroot environment acts like a sandbox, allowing you to build and test packages in isolation. This minimizes the risk of conflicts and ensures a clean build process.
Secure Ftp Services
FTP servers are often targets for attacks. By setting up a chroot jail, you can ensure that even if an FTP account is compromised, the attacker won’t access the entire file system. This layer of security can be crucial for businesses that handle sensitive information.
Are you already considering how a chroot jail can make your system more robust? Whether it’s securing a server or creating a safe development environment, the possibilities are extensive. With these practical use cases, you can start leveraging chroot jails effectively in your Linux setup.
Frequently Asked Questions
How To Setup Chroot In Linux?
To set up chroot in Linux, create a new directory for the environment. Install necessary binaries and libraries. Use the chroot command to change the root directory to the new one. Ensure proper permissions and configurations for secure usage.
What Is The Alternative To Chroot Jail?
An alternative to chroot jail is using containers like Docker, which offer isolation and resource control. Virtual machines also provide a secure environment for applications. They enhance security and simplify deployment compared to traditional chroot methods. Consider using SELinux or AppArmor for added security layers.
How To Create A Chroot Directory?
To create a chroot directory, use the command mkdir /path/to/chroot. Copy necessary files and libraries into this directory. Use chroot /path/to/chroot to enter the chroot environment. Ensure proper permissions and ownership for security.
Why Is Chroot Called Jail?
Chroot is called a jail because it isolates programs, limiting their access to a specific directory. This containment prevents unauthorized access to the broader system, similar to how a physical jail confines individuals. It enhances security by restricting the execution environment of applications.
Conclusion
Setting up a chroot jail in Linux enhances system security. It isolates applications, protecting your main system. Follow the steps carefully to ensure success. Double-check configurations to avoid errors. Practice regularly to gain confidence. A secure environment benefits everyone. Your system becomes more robust and reliable.
Remember, every step matters in security. Keep learning and exploring Linux features. Understanding chroot jails strengthens your skills. Stay updated with the latest Linux security practices. This knowledge helps in managing complex systems efficiently. Embrace the learning journey and enjoy the process.
Happy computing!
-

 DevOps6 years ago
DevOps6 years agoSaltstack Tutorial for beginners [2025]
-

 DevOps6 years ago
DevOps6 years agoHow to build a Docker cron job Container easily [2025]
-

 Linux7 years ago
Linux7 years agomail Command in Linux/Unix with 10+ Examples [2025]
-

 DevOps6 years ago
DevOps6 years agoDocker ADD vs COPY vs VOLUME – [2025]
-
 DevOps6 years ago
DevOps6 years agoHow to setup Pritunl VPN on AWS to Access Servers
-

 Linux7 years ago
Linux7 years agoGrep Command In Unix/Linux with 25+ Examples [2025]
-

 Linux7 years ago
Linux7 years agoFind command in Unix/Linux with 30+ Examples [2025]
-
Linux5 years ago
How To setup Django with Postgres, Nginx, and Gunicorn on Ubuntu 20.04

