DevOps
How to Use Iptables to Set Up a Basic Firewall: Step-by-Step Guide
Imagine waking up one day to find your computer compromised, your data exposed, or your personal information stolen. It’s a chilling thought, isn’t it?
That’s why you need a reliable firewall to protect your system from the myriad threats lurking online. Enter Iptables, a powerful tool that can help secure your computer effectively. By understanding how to use Iptables, you can set up a basic firewall to safeguard your digital life.
This guide will walk you through the process, ensuring you gain the confidence to shield your system from unwanted intrusions. Don’t leave your computer vulnerable; learn how to take control and protect what matters most to you. Keep reading to discover how Iptables can be your first line of defense against cyber threats.
What Is Iptables?
Iptables is a command-line utility for Linux operating systems. It manages and configures the firewall settings of the system. Understanding its function is crucial for anyone dealing with network security. Iptables helps in filtering traffic based on predefined rules. These rules determine how packets are handled by the system.
What Makes Iptables Essential?
Iptables plays a pivotal role in network security. It allows users to define rules for traffic control. These rules can block or allow packets through the firewall. This helps in protecting the system from unauthorized access. Users can set up chains of rules to manage incoming and outgoing traffic. This flexibility makes it a preferred choice for many.
How Does Iptables Work?
Iptables work by using tables to store rules. These tables contain chains, which are lists of rules. Each chain handles packets in different stages of their journey. When a packet arrives, it is checked against these rules. If it matches, the rule action is applied. If not, it moves to the next rule. This process is quick and efficient. Iptables use this mechanism to ensure security.
Why Choose Iptables For Firewall Setup?
Choosing Iptables for firewall setup offers several benefits. It provides granular control over network traffic. Users can customize rules according to their needs. This ensures that only legitimate traffic passes through. It also allows logging, which helps in monitoring and analysis. The simplicity and effectiveness of Iptables make it a reliable choice.

Credit: help.ovhcloud.com
Benefits Of Using Iptables
Setting up a basic firewall with Iptables enhances network security by controlling traffic flow. Iptables allows customization of rules to permit or block specific connections, ensuring optimal protection against unauthorized access. Simple yet effective, it provides a robust foundation for safeguarding your system.
Setting up a firewall is crucial for protecting your server from malicious attacks. Iptables is a powerful tool that helps you achieve just that by managing the Linux kernel’s netfilter framework. It may seem technical at first, but once you understand its benefits, you’ll see why it’s worth your time.Unmatched Flexibility
Iptables offers incredible flexibility in configuring rules for your firewall. You have the freedom to specify conditions based on IP addresses, protocols, ports, and even packet states. This means you can tailor your firewall precisely to the needs of your network. Imagine being able to block unwanted traffic while allowing legitimate connections seamlessly. For example, you can permit SSH access only from specific IP addresses, adding an extra layer of security.Enhanced Security
Using Iptables, you can significantly enhance the security of your network. By setting up specific rules, you can prevent unauthorized access and protect sensitive data. How secure do you feel knowing that your server is guarded by a custom-made firewall? You can stop attacks in their tracks by blocking suspicious traffic and allowing only trusted sources. This proactive approach can save you from potential breaches and costly damages.Cost-effective Solution
Iptables is a built-in feature in most Linux distributions, making it a cost-effective solution for setting up a firewall. You don’t need to purchase expensive software to keep your network secure. With some time investment and the right guidance, you can leverage Iptables without additional financial burden. It’s a reliable option for individuals or small businesses looking to protect their servers without breaking the bank.Community And Support
The Linux community is vast and resourceful, offering plenty of support for Iptables users. From forums to tutorials, there’s a wealth of information to help you master Iptables. Have you ever felt stuck while configuring a firewall? Chances are, someone has faced the same issue and shared their solution online. This communal knowledge can be a valuable asset as you navigate your firewall setup.Real-time Monitoring
Iptables provides real-time monitoring capabilities, allowing you to keep an eye on the traffic flowing through your network. This visibility is crucial for identifying and addressing potential threats promptly. Wouldn’t it be reassuring to know what’s happening on your server at any given moment? You can detect unusual patterns and take immediate action, ensuring your network remains secure and efficient. Iptables is not just about blocking or allowing traffic. It’s about empowering you to take control of your network security with precision and confidence. Dive into the world of Iptables, and discover how it can transform your approach to safeguarding your digital space.Installing Iptables On Your System
Setting up a firewall is crucial for system security. Iptables is a powerful tool for managing network traffic. Before configuring rules, you need to install Iptables. This section guides you through the installation process.
Installing Iptables On Ubuntu
First, open the terminal on your Ubuntu system. Type sudo apt-get update to refresh package lists. Then, install Iptables by typing sudo apt-get install iptables. Wait for the installation to complete.
Installing Iptables On Centos
Begin by accessing your CentOS terminal. Run yum update to update packages. Install Iptables by executing yum install iptables-services. Confirm the installation when prompted.
Verifying Iptables Installation
After installation, verify by typing iptables --version. This command displays the installed version. Ensure the output confirms Iptables is active.
Starting Iptables Service
For Ubuntu, use sudo systemctl start iptables. On CentOS, type systemctl start iptables. Check the service status with systemctl status iptables. Ensure the service is running.
Basic Iptables Commands
Setting up a basic firewall with Iptables involves using straightforward commands. These commands help control network traffic by allowing or blocking specific connections. Understanding basic rules enables you to protect your system efficiently and maintain security.
Setting up a basic firewall with Iptables can seem daunting, but understanding the fundamental commands can simplify the process. Iptables is a powerful utility that allows you to control the incoming and outgoing traffic on your server. Mastering a few basic commands can help you maintain a secure environment. Whether you’re a seasoned admin or a beginner, learning how to manage Iptables effectively is crucial for server security. Let’s dive into some key commands that you need to know. ###Listing Current Rules
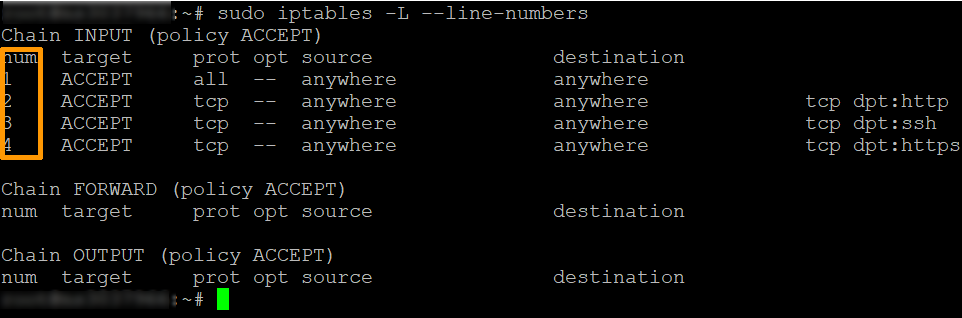
Knowing the current configuration of your firewall is essential. You can easily list all the current rules with a simple command. Just type `sudo iptables -L` in your terminal. This displays all active rules and their order of execution. It’s like taking a snapshot of your firewall’s current state. You can see which rules are active and how packets are being processed. Have you ever wondered why some traffic is allowed while others are blocked? This command can help answer that. ###Flushing Existing Rules
Sometimes, you need a clean slate. Flushing existing rules removes all current configurations, allowing you to start fresh. Use the command `sudo iptables -F` to clear out existing rules. This is particularly useful if you’ve made several changes and want to avoid conflicting rules. Imagine you’re rearranging a cluttered desk; flushing clears the clutter. It’s a quick way to reset your firewall settings. ###Saving Current Rules
After setting up your rules, it’s crucial to save them. Without saving, any changes will be lost after a reboot. Use `sudo iptables-save > /etc/iptables/rules.v4` to save the current configuration. Think of it as hitting the save button on your important document. You wouldn’t want to lose your work, would you? Saving ensures your firewall remains secure even after a restart. Is your server protected enough to withstand a reboot? By mastering these commands, you can effectively manage your firewall’s rules and ensure your server’s security. What other commands have you found useful in managing Iptables?Setting Default Policies
Configuring default policies in iptables shapes your firewall’s behavior. Default policies determine how packets are treated. You can choose to accept, drop, or reject packets. Each option serves a distinct purpose. Understanding these choices enhances your firewall’s efficiency. Learn how to set these policies effectively.
Accept Policy
The accept policy allows packets to pass through. It is used when you want unrestricted access. Setting the default policy to accept makes communication smooth. But it can open your system to vulnerabilities. Choose this option carefully and review your security needs.
Drop Policy
Drop policy discards packets silently. No response is sent to the sender. This choice strengthens security. Unwanted traffic is blocked without notifying attackers. Use drop policy when you need high security. It keeps your network safe but requires careful rule setting.
Reject Policy
Reject policy blocks packets and sends an error message back. It informs senders their packets are not welcomed. This option is useful for notifying legitimate users of access issues. It prevents confusion and alerts users about blocked connections. Implement reject policy to maintain transparency.
Credit: help.ovhcloud.com
Creating Basic Rules
Setting up a basic firewall using iptables can enhance security. Define rules to manage incoming and outgoing traffic. Control data flow to protect your system effectively.
Setting up a basic firewall with iptables is crucial for security. It controls incoming and outgoing traffic. Knowing how to create rules is essential. These rules help manage your network’s safety. Let’s explore some basic configurations.Allowing Incoming Traffic
To allow specific incoming traffic, you need to define rules. Start by identifying the type of traffic you want to allow. Use the iptables command to permit trusted connections. This keeps your system accessible to safe traffic. Ensure that only necessary services are allowed through.Blocking Specific Ip Addresses
Sometimes, blocking specific IP addresses is necessary. This prevents unwanted traffic from reaching your system. Use iptables to specify the IP addresses to block. This step enhances your firewall’s effectiveness. It helps protect against potential threats.Allowing Specific Ports
Allowing traffic on specific ports is another crucial task. Identify which ports need to be open for your services. Use iptables to allow these ports. This ensures that essential services run smoothly. Keep unused ports closed to enhance security. “`Testing Your Firewall
Setting up a basic firewall with Iptables enhances your system’s security. Iptables filters traffic by defining rules. These rules decide which data packets can enter or leave your network.
Testing your firewall is a crucial step to ensure that your security configurations are working as expected. Imagine setting up a protective barrier around your digital fortress only to find out it’s full of holes. By testing your firewall, you can identify vulnerabilities and tighten your defenses. Let’s dive into the practical steps to verify your firewall settings with iptables.Verify Your Rules
Begin by reviewing the rules you’ve implemented in iptables. Use the command `iptables -L -v` to display the list of rules. This command provides a detailed view, including packet counts, to help you understand how traffic is being handled. Are there any unexpected rules? Look for any anomalies or rules that don’t align with your intended security posture. Adjust as necessary to fortify your firewall.Conduct Port Scans
A port scan can reveal open ports that shouldn’t be accessible. Tools like Nmap can be used to scan your system. Run a simple scan with `nmapTest Specific Rules
Testing specific rules ensures they are functioning correctly. If you’ve set rules to allow or block certain IP addresses, test these scenarios using `curl` or `ping` from the allowed or blocked IPs. Were you able to access services you meant to block? If so, revisit your iptables configuration to correct any errors.Simulate Attacks
Simulating attacks can provide insights into how well your firewall stands against potential threats. Use penetration testing tools like Metasploit or Kali Linux to test your firewall’s resilience. How did your firewall hold up? If vulnerabilities were exploited, it’s time to reinforce your rules and configurations to better protect your system.Monitor Logs
Regularly monitoring firewall logs can help you catch unusual activity. Use the `dmesg` or check logs located in `/var/log/` to review any suspicious entries. What do the logs reveal? If there’s unexpected traffic, it might be necessary to adjust your firewall settings or further investigate potential threats. Testing your firewall with iptables isn’t just a one-time task. It’s an ongoing process that keeps your defenses robust. Are you ready to commit to regular testing and monitoring? Your digital security depends on it!Persisting Iptables Rules
Secure your system by using Iptables to set up a basic firewall. Easily manage and persist your Iptables rules across reboots. Maintain consistent protection with simple commands and ensure your firewall settings are always active.
Persisting iptables rules is a crucial step in ensuring your firewall configurations remain intact after a system reboot. Imagine spending hours meticulously setting up your firewall rules, only to see them vanish after a restart. Frustrating, right? That’s why understanding how to save and restore iptables settings is essential for maintaining a secure server environment. Let’s dive into the practical steps to make your iptables rules persist. ###Using Iptables-save And Iptables-restore
One effective way to preserve your rules is by using the `iptables-save` and `iptables-restore` commands. These tools allow you to export your current iptables configuration to a file and reload it when needed. Start by saving your current rules with `iptables-save`: “`bash sudo iptables-save > /etc/iptables/rules.v4 “` This command writes the current iptables rules to the file `rules.v4`. You can choose a different location or name, but ensure it’s a secure and accessible directory. To restore the rules, use `iptables-restore`: “`bash sudo iptables-restore < /etc/iptables/rules.v4 “` This command reads the configuration from `rules.v4` and applies it to your iptables. It’s a quick way to reinstate your firewall settings after a reboot. ###Automating Rule Persistence
Manual restoration can be tedious. Automating the process saves time and reduces errors. You can automate rule persistence by configuring your system to restore rules during boot. Edit your system’s boot script to include `iptables-restore`. For Ubuntu systems, you might add it to `/etc/rc.local`: “`bash iptables-restore < /etc/iptables/rules.v4 “` Alternatively, create a system service. Using `systemd`, you can set up a service to restore your rules automatically: 1. Create a new service file: `/etc/systemd/system/iptables.service`. 2. Add the following content: “`ini [Unit] Description=Restore iptables rules [Service] ExecStart=/sbin/iptables-restore < /etc/iptables/rules.v4 [Install] WantedBy=multi-user.target “` Enable the service with: “`bash sudo systemctl enable iptables.service “` This method ensures your rules are applied every time your system boots. ###Testing Your Configuration
After setting up persistence, test your configuration to ensure it works as expected. Reboot your system and check if your rules are still active. Use `sudo iptables -L` to list current rules. If they match your saved configuration, you’ve successfully persisted your iptables rules. What happens if your rules don’t load? Investigate potential issues by checking for typos or incorrect paths in your scripts. Debugging might be necessary, but it’s a valuable learning experience. ###Final Thoughts
Persisting iptables rules can be a game changer for your server’s security. By automating this process, you save time and protect your system from vulnerabilities. So, what’s your next step? Test these methods on your server and see the difference in maintaining a reliable firewall. How secure do you want your server to be? Let that question guide your actions.Troubleshooting Common Issues
Troubleshooting common issues in iptables can be challenging. Yet, understanding the basics can help you maintain a secure firewall. Often, minor mistakes can cause significant problems. Addressing these quickly ensures your network stays protected. Below, we explore common issues and how to resolve them.
Checking Rule Syntax
Incorrect syntax can lead to iptables rules not working. Always double-check your rule syntax. Use the iptables -L command to list current rules. It helps identify any syntax errors. Make sure every command follows the correct format. Missing or extra characters can disrupt the rules.
Verifying Rule Order
The order of rules in iptables affects how they function. Rules are processed from top to bottom. The first matching rule takes effect. Incorrect order can cause unexpected behavior. Always review the rule sequence. Use iptables -L --line-numbers to see rules with their order. Adjust as needed to ensure proper rule execution.
Enhancing Firewall Security
Enhancing firewall security is crucial for safeguarding your network against potential threats. As you delve deeper into using iptables, simple configurations can transform into robust defenses. This section focuses on two essential techniques: logging and rate limiting. These are not just technical steps but powerful strategies to fortify your firewall.
Using Logging
Logging is like having a CCTV camera for your network. It lets you monitor and record activities, giving you insight into what’s happening. To enable logging, you add specific rules in iptables that log packets.
Imagine catching an intruder in the act. When packets match certain criteria, they get logged, offering you a detailed view. This can help you detect unusual patterns or potential breaches. You can use commands like:
iptables -A INPUT -j LOG --log-prefix "IPTABLES INPUT: "This command logs all incoming packets, helping you spot suspicious activity. Are you seeing too many requests from a single IP? Logging can make this apparent, prompting you to investigate further.
Implementing Rate Limiting
Have you ever received a flood of emails from a single sender? Rate limiting in iptables works similarly, controlling the flow of traffic to prevent overloads. It’s like setting a speed limit on your network highway.
By implementing rate limiting, you can restrict the number of connections or packets per second. This can prevent denial-of-service attacks where your server gets overwhelmed with requests. Consider using the following command:
iptables -A INPUT -p tcp --dport 22 -m limit --limit 5/minute -j ACCEPTThis rule limits SSH connections to five per minute, ensuring your server remains responsive and secure. Think about your network’s capacity and adjust limits to balance security and performance.
Have you experienced sudden slowdowns or outages? Rate limiting can be your shield, maintaining stability and preventing disruptions. It’s not just about limiting; it’s about maintaining control and ensuring reliability.
How can you leverage these techniques to enhance your firewall security? Logging and rate limiting are more than just technical jargon; they are your tools to build a resilient defense. Consider incorporating them into your firewall strategy. What security challenges are you facing, and how can these techniques help you address them?

Credit: systemweakness.com
Frequently Asked Questions
How To Create A Firewall Using Iptables?
To create a firewall using iptables, define rules specifying allowed and blocked traffic. Use `iptables -A` to add rules. For example, `iptables -A INPUT -p tcp –dport 22 -j ACCEPT` allows SSH. Save configurations with `iptables-save`. Regularly update rules to enhance security and monitor traffic effectively.
What Is The Basic Firewall Iptables?
Iptables is a command-line firewall utility in Linux. It manages incoming and outgoing traffic. Users can define rules to accept, drop, or forward packets. It’s essential for network security, offering flexibility and control. Iptables operates at the network layer, providing vital protection against unauthorized access.
How To Configure Basic Firewall?
Access your firewall settings through your router or operating system. Enable basic protection features. Create rules to allow or block specific traffic types. Regularly update firewall software to ensure optimal security. Save and apply your configuration changes.
Is Iptables A Good Firewall?
Yes, iptables is a good firewall. It offers robust security features for Linux systems. Users can customize rules to manage network traffic effectively. Its flexibility and reliability make it popular among system administrators. Iptables supports advanced filtering, making it suitable for various security needs.
Conclusion
Setting up a basic firewall with Iptables enhances security. It’s crucial for protecting your server and data. Start with simple rules. Block unwanted traffic. Allow only necessary connections. Regularly update and review your rules. This ensures ongoing protection. Practice regularly to become confident.
Iptables can seem complex initially. But, with time, it gets easier. Remember, a secure server is a safe server. Stay vigilant and proactive in maintaining your firewall. Security is an ongoing process. Keep learning and adapting to new threats. Your efforts will keep your system safe.
-

 DevOps6 years ago
DevOps6 years agoSaltstack Tutorial for beginners [2025]
-

 DevOps6 years ago
DevOps6 years agoHow to build a Docker cron job Container easily [2025]
-

 Linux7 years ago
Linux7 years agomail Command in Linux/Unix with 10+ Examples [2025]
-

 DevOps6 years ago
DevOps6 years agoDocker ADD vs COPY vs VOLUME – [2025]
-
 DevOps6 years ago
DevOps6 years agoHow to setup Pritunl VPN on AWS to Access Servers
-

 Linux7 years ago
Linux7 years agoGrep Command In Unix/Linux with 25+ Examples [2025]
-

 Linux7 years ago
Linux7 years agoFind command in Unix/Linux with 30+ Examples [2025]
-
Linux6 years ago
How To setup Django with Postgres, Nginx, and Gunicorn on Ubuntu 20.04

