DevOps
Securing a Linux Server: Hardening Guide for Maximum Safety
Imagine this: your Linux server is like a fortress. It’s the stronghold of your digital realm, safeguarding precious data and vital operations.
But even the mightiest fortresses need reinforcement against potential threats. That’s where securing your Linux server through hardening comes into play. You might wonder why this is crucial. Simply put, the internet is swarming with potential threats, from hackers to malware.
Your server, if left unprotected, can become an easy target. But fear not, because with the right strategies and tools, you can transform your server into an impregnable fortress. This guide will take you step-by-step through practical and effective measures to harden your Linux server. You’ll learn how to tighten security, close loopholes, and ensure your server runs smoothly and safely. Whether you’re a seasoned administrator or just starting out, this guide will equip you with the knowledge to protect your server against lurking dangers. Stay with us as we dive into the essential techniques that will keep your server secure and your mind at ease. Your journey to a fortified Linux server starts here.
.jpg?width=1280&auto=webp&quality=95&format=jpg&disable=upscale)
Credit: www.itprotoday.com
Initial Setup And Configuration
Setting up a Linux server is a crucial step in securing your digital assets. During the initial setup and configuration, you lay the foundation for your server’s security. It’s like building a house; you want to ensure the walls are strong, the doors are locked, and there’s no easy way for intruders to get in. Let’s dive into how you can achieve this with your Linux server.
Choosing A Secure Linux Distribution
Your choice of Linux distribution can impact your server’s security. Opt for distributions known for robust security features.
Consider Ubuntu Server or CentOS, which are popular for their stability and security. These distributions offer regular updates and have strong community support.
Think about what specific needs your server has. Do you need a lightweight option, or is a broader feature set more important? Choosing wisely can save you headaches down the road.
Updating System Packages
Keeping your system packages up-to-date is like ensuring your car has regular check-ups. It’s crucial for maintaining security.
Run the update command regularly to keep everything patched against vulnerabilities. This simple step can prevent many security issues.
Automate updates if you can. This ensures your system is always running the latest versions without manual intervention.
Creating A Non-root User
Operating as the root user is risky business. It’s like giving the keys to your entire kingdom to just anyone.
Create a non-root user for daily tasks. This limits the potential damage if the account is compromised.
Use commands like adduser and usermod to set up and configure your new user. It’s a small step that significantly boosts security.
What measures have you taken to secure your server’s initial setup? Share your experiences and insights in the comments below. Your feedback might just be the key to someone else’s security success!
Network Security
Securing your Linux server is crucial, especially when it comes to network security. The network is the first entry point for potential threats, and keeping it secure can be the difference between a vulnerable system and a fortified one. Whether you’re a seasoned sysadmin or a newcomer to server management, understanding network security is essential. Let’s dive into some practical strategies to enhance your Linux server’s defenses.
Configuring A Firewall
Think of a firewall as your server’s gatekeeper. It decides what traffic gets in and what stays out. Setting up a firewall on your Linux server is a straightforward yet powerful way to protect your system.
Start by identifying the traffic you need. Allow only necessary connections, such as HTTP/HTTPS for web servers. Tools like UFW (Uncomplicated Firewall) make configuring firewalls user-friendly, even for beginners. By default, block all incoming connections and selectively open ports as needed.
Have you ever noticed suspicious activity in your server logs? A properly configured firewall can help prevent unauthorized access before it even reaches your server. How are you managing your server’s incoming and outgoing traffic?
Disabling Unused Network Services
Every service running on your server is a potential entry point for attackers. Evaluate your server’s active services and disable any that aren’t needed. This simple step reduces the attack surface significantly.
Consider a server that was compromised due to an outdated FTP service running unnoticed. This could have been prevented by regularly auditing and shutting down unused services. Use tools like netstat or ss to review active services. Then, disable them using systemctl or service commands.
Are there services running on your server that you don’t use? Take control and deactivate them before they become a liability.
Securing Ssh Access
SSH is the primary method for remote server management, but it can be a target for attackers. Strengthening SSH access is vital for your server’s security.
Start by changing the default port from 22 to a random one. This simple trick can deter automated attacks. Additionally, disable root login and use key-based authentication instead of passwords. This adds an extra layer of security.
I once faced repeated login attempts on a server until I strengthened SSH configurations. Have you considered the security implications of using default settings? Take proactive steps to secure your SSH access.
Network security is not just about technology—it’s about vigilance and proactive measures. How are you ensuring your server is safe from potential threats?
File System And Access Control
Protecting Linux servers involves configuring file systems and access controls. Implement strong permissions to restrict unauthorized access. Regular audits help ensure security policies are in place.
Securing your Linux server is crucial to protect sensitive data and maintain system integrity. One fundamental aspect is the File System and Access Control. Without proper management, your server becomes vulnerable to unauthorized access and data breaches. By focusing on strong password policies, file permissions, ownership, and encryption, you can significantly enhance your server’s security.Implementing Strong Password Policies
Passwords are your first line of defense. Weak passwords are akin to leaving your front door unlocked. Set guidelines for creating strong passwords. Encourage using a mix of letters, numbers, and symbols. Consider using passphrases for added complexity. Regularly updating passwords reduces the risk of compromise. Implement password expiration policies to ensure users change passwords periodically. Use tools like `chage` to manage password aging and enforce your policies effectively. Remember, a robust password policy isn’t just about complexity; it’s about regular updates and user awareness.Using File Permissions And Ownership
File permissions dictate who can read, write, or execute files on your server. Misconfigured permissions can lead to unauthorized access. Utilize Linux commands like `chmod` and `chown` to set appropriate permissions and ownership. Only give users the access they need, no more. Adopt the principle of least privilege. Check permissions regularly using `ls -l` and adjust as necessary. A colleague once shared how a small oversight in permissions led to a massive data leak. Don’t let it happen to you. Pay attention to the details.Encrypting Sensitive Data
Encryption is a powerful tool for protecting sensitive data. It ensures that even if data is accessed, it remains unreadable without the encryption key. Implement encryption for data at rest using tools like `LUKS` or `dm-crypt`. Encrypt backups and sensitive files to prevent unauthorized access. Consider encrypting data in transit using protocols like SSL/TLS. This protects data as it moves between servers or clients. Ask yourself: Is my sensitive data secure from prying eyes? If the answer is no, encryption should be your next step. Taking these actions will bolster your Linux server’s security. Are you ready to take control and safeguard your data?
Credit: 63sats.com
Software And Service Security
Securing a Linux server involves implementing robust security measures like firewalls and regular updates. Disabling unnecessary services enhances protection against vulnerabilities. Using strong passwords and encryption adds an extra layer of defense.
Securing a Linux server involves more than just installing a firewall and calling it a day. It’s crucial to ensure that the software and services running on your server are secure. Weaknesses in these areas can expose your server to vulnerabilities. Whether you’re a seasoned sysadmin or a beginner, you need to understand the importance of software and service security. Let’s dive into some practical steps you can take to bolster this aspect of your server’s security.Regular Software Updates
Keeping your software updated is one of the simplest yet most effective security measures. Outdated software can be a goldmine for hackers, as they often exploit known vulnerabilities in older versions. Take a moment to check your server’s update settings. Are you receiving notifications for updates? If not, configure your server to alert you. Regular updates ensure that any security patches are promptly applied. Consider automating this process. Set up a cron job to regularly check for updates. This way, your system stays secure without manual intervention, freeing up your time for other tasks.Using Intrusion Detection Systems
Intrusion Detection Systems (IDS) are like having a security guard for your server. They monitor and alert you to suspicious activities. But are you using one? Imagine getting an alert when someone tries to access your server without permission. An IDS can provide this level of security. Tools like Fail2Ban or Snort are popular choices among Linux users. Don’t just install an IDS; configure it properly. Customize the alerts to suit your needs. Regularly review the logs to understand what threats your server might face. This proactive approach can save you from potential headaches.Isolating Services With Containers
Containerization is a game-changer in service security. It allows you to isolate applications, reducing the risk of one service affecting others. Think of it as creating a separate room for each service. If something goes wrong in one room, the others remain untouched. Docker is a widely used tool for this purpose. Containers also simplify the deployment process. You can quickly spin up a new service without affecting existing ones. Explore container orchestration tools like Kubernetes for larger, more complex setups. But before diving into containers, ask yourself: How isolated are your services? By focusing on these areas, you can significantly improve the security of your Linux server. Remember, a secure server is not just about tools—it’s about consistently applying best practices. How will you enhance your server’s security today?Monitoring And Logging
Ensuring a Linux server’s security involves monitoring activities and logging events continuously. These practices detect unusual behavior and unauthorized access attempts. Implementing effective tools and strategies helps maintain server integrity, protecting sensitive data from threats.
Securing a Linux server is a critical task, and monitoring and logging play a vital role in this process. By keeping a close eye on your server’s activities, you can swiftly detect suspicious behavior and take action before any serious damage occurs. Imagine your server as a busy airport; every movement needs to be tracked to ensure everything runs smoothly. So how can you keep your server in check? Let’s dive into the essentials of monitoring and logging.Setting Up System Logs
Setting up system logs on your Linux server is like installing security cameras in your home. They capture everything happening on your server, from system errors to user logins. Tools like syslog, rsyslog, or systemd-journald can help you record these events. Ensure your logs are stored securely and are easily accessible for review. Log rotation is a must to prevent your server from running out of space. Regularly checking these logs can help you catch potential issues before they escalate.Monitoring User Activity
Understanding who does what on your server is crucial. Monitoring user activity helps you track legitimate and potentially harmful actions. Use commands like `last` and `who` to see who is logged in and what they are doing. Consider setting up tools like auditd to get detailed reports on user actions. This might seem like extra work, but knowing what your users are up to can save you from dealing with a security breach later on.Analyzing Log Files For Anomalies
Analyzing log files can seem daunting, but it’s an essential step in server security. Look for patterns or unusual activity that might indicate a problem. Are there repeated failed login attempts? That could be a brute force attack. Tools like Logwatch or GoAccess can help simplify this process. They provide insights into potential security threats by highlighting anomalies. Make it a habit to review these reports regularly. Are you seeing something odd? Don’t ignore it—investigate promptly. Are you keeping a close eye on your server’s health? Implement these monitoring and logging practices to ensure your Linux server remains secure and robust.Backup And Recovery
Ensuring data safety is crucial in securing a Linux server. Backup and recovery are essential processes to safeguard your data. A robust backup strategy helps restore your server after unexpected failures. Planning and testing are key to effective data recovery.
Establishing A Backup Strategy
Begin with a clear backup plan. Identify critical data that needs protection. Choose backup tools compatible with your Linux server. Regularly schedule backups to avoid data loss. Use automation for consistent backups without manual intervention.
Testing Backup Restorations
Regularly test your backups by performing restorations. Ensure data integrity and accessibility. Testing helps identify issues before an actual disaster. Document the restoration process for quick recovery. Keep logs of successful and failed restorations.
Offsite Data Storage
Store backups in a secure offsite location. This protects data from local threats. Use cloud services or physical storage for offsite backups. Encrypt data to enhance security. Regularly update and manage offsite storage solutions.
Advanced Security Measures
Enhance your Linux server’s security by implementing advanced measures like firewall configurations and regular software updates. Protect against unauthorized access through strong passwords and encryption techniques. Regularly monitor logs for suspicious activities to ensure robust defense against cyber threats.
Securing a Linux server is an ongoing process, especially as threats evolve. While basic security measures lay the foundation, advanced security measures elevate your server’s defense to a new level. These measures require a deeper understanding and some hands-on configuration, but the payoff is a more robust, resilient system. Are you ready to take your server’s security to the next level?Implementing Selinux Or Apparmor
Choosing between SELinux and AppArmor can feel like picking a side. Both are powerful tools for enhancing Linux security, yet they operate differently. SELinux, short for Security-Enhanced Linux, enforces strict access controls and is known for its comprehensive security policies. It can be intimidating at first, but once configured, it offers peace of mind against unauthorized access. Have you ever wondered how a small misconfiguration could leave your server vulnerable? SELinux is designed to prevent such slip-ups. On the other hand, AppArmor provides a more straightforward approach, focusing on application-level security. It uses profiles to define what applications can do, making it easier for beginners to grasp. I remember my first encounter with AppArmor—it was a relief to see how easily I could restrict an application’s access to sensitive parts of the system. Which tool aligns better with your comfort level and needs?Enforcing Mandatory Access Controls
Mandatory Access Controls (MAC) are all about defining who can access what. Unlike discretionary access controls, MAC policies are non-negotiable, adding a layer of rigidity to your security protocols. Implementing MAC can prevent users, including administrators, from making changes that could compromise the system. Imagine a scenario where a rogue application tries to modify system files—MAC ensures it hits a wall. It’s like having a security guard that follows rules to the letter. Consider starting with a basic policy and gradually tightening it as you understand your system’s needs better. Have you considered how much control you’re willing to relinquish for improved security?Using Security Auditing Tools
Security auditing tools are your best allies in spotting vulnerabilities before they become breaches. They scan your system, highlight weaknesses, and often suggest fixes. Tools like Lynis and OpenSCAP can be invaluable. I recall running Lynis for the first time; it pointed out several overlooked configurations that could have been exploited. These tools can act as an extra set of eyes, ensuring nothing slips through the cracks. Regular audits can catch new vulnerabilities and confirm that previous issues remain resolved. When was the last time you checked your server’s defenses? With these tools, you can maintain an ongoing security posture that adapts to new threats. Incorporating these advanced measures can seem daunting, but each step strengthens your server’s defense. As you explore these options, remember that the goal is a balance between security and functionality. What steps will you take today to fortify your Linux server?
Credit: www.ceos3c.com
Frequently Asked Questions
How Do You Harden A Linux Server?
To harden a Linux server, update software regularly, disable unused services, and configure a firewall. Use strong passwords, enable SSH key authentication, and restrict root access. Monitor logs and implement intrusion detection systems for added security.
How To Make A Linux Server Secure?
Secure a Linux server by updating software regularly, configuring firewalls, using SSH keys, disabling root access, and monitoring logs.
What Are Your First Three Steps When Securing A Linux Server?
First, update the server and install essential security patches. Second, configure a firewall to block unauthorized access. Third, disable root login and use SSH keys for authentication.
What Is The First Step To Take When Hardening A Linux System?
The first step to harden a Linux system is to update and patch all software. Regularly check for security updates. Install the latest security patches promptly to protect against vulnerabilities. This ensures your system remains secure and up-to-date.
Conclusion
Securing a Linux server is crucial for data protection. Simple steps can enhance server safety. Regular updates are key. Use strong passwords for all accounts. Monitor server activities frequently. Firewalls add another layer of security. Backups ensure data recovery. Access control limits who can enter.
Encryption protects sensitive information. Following these practices helps safeguard your server. Stay vigilant and proactive. Security is a continuous process. Make it a priority. Your server and data will thank you.
-

 DevOps6 years ago
DevOps6 years agoSaltstack Tutorial for beginners [2025]
-

 DevOps6 years ago
DevOps6 years agoHow to build a Docker cron job Container easily [2025]
-

 Linux7 years ago
Linux7 years agomail Command in Linux/Unix with 10+ Examples [2025]
-

 DevOps6 years ago
DevOps6 years agoDocker ADD vs COPY vs VOLUME – [2025]
-
 DevOps6 years ago
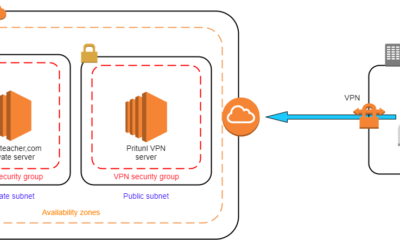
DevOps6 years agoHow to setup Pritunl VPN on AWS to Access Servers
-

 Linux7 years ago
Linux7 years agoGrep Command In Unix/Linux with 25+ Examples [2025]
-

 Linux7 years ago
Linux7 years agoFind command in Unix/Linux with 30+ Examples [2025]
-
Linux6 years ago
How To setup Django with Postgres, Nginx, and Gunicorn on Ubuntu 20.04

