Linux
What is the Root User in Linux? Uncover Its Secrets
Imagine having the keys to the kingdom where you can unlock every door and access every secret. In the world of Linux, the root user is that powerful entity.
But what does it mean to be the root user? Why is it so important for you to understand this concept if you’re diving into the Linux environment? Whether you’re curious about maximizing your system’s potential or ensuring its security, knowing about the root user can empower you in ways you might not expect.
This article will unravel the mysteries behind the root user, helping you grasp its significance and how it impacts your Linux experience. Read on to discover how mastering the role of the root user can transform the way you interact with your Linux system.
Role Of The Root User
The root user in Linux holds a powerful position. This user has complete control over the system. They can access, modify, and manage all files and settings. This authority is crucial for system management and maintenance. Understanding the role of the root user is essential for anyone interacting with Linux systems.
Access To All Files And Directories
Root user can access every file and directory. No restrictions apply to their permissions. This unrestricted access allows the root user to perform any needed tasks. From system configurations to security checks, everything is possible.
Installation And Management Of Software
Software installation often requires root access. The root user can install, update, and remove software. This role ensures that necessary tools are available for users. Managing software effectively keeps the system running smoothly.
System Configuration And Maintenance
Root user configures system settings. They adjust network settings, user permissions, and storage options. Maintenance tasks like backups and updates require root access. Proper configuration ensures system stability and efficiency.
Security Management And User Control
The root user manages security protocols. They set permissions and monitor user activities. This control helps protect the system from unauthorized access. User management is key to maintaining a secure environment.
Credit: www.scaler.com
Privileges Of The Root User
Understanding the privileges of the root user in Linux can open up a whole new world for you. Imagine having the power to control everything on your system, from installing software to changing configurations. But with great power comes great responsibility. You need to be cautious when using root privileges to avoid potential risks like system damage or security vulnerabilities. So, what exactly can the root user do?
Full Access To The File System
The root user enjoys unrestricted access to every file and directory on the system. Whether you want to edit system files, delete directories, or move important data, root privileges allow you to do so without any limitations. This is crucial for system administrators who need to perform maintenance tasks. However, it’s important to be careful; one wrong command can lead to disastrous consequences.
User And Group Management
As a root user, you have the authority to add, delete, or modify user accounts and groups. This means you can manage who has access to the system and what they can do. Imagine the power to create new user accounts for team members or restrict access for security reasons. It’s your responsibility to ensure that user permissions are correctly set to maintain system security.
Software Installation And Removal
Root privileges allow you to install or remove software packages on your Linux system. Have you ever wanted to try out a new application, but your system restrictions held you back? As root, you can install any software without waiting for permissions. However, it’s wise to verify the source of software to avoid potential security risks.
System Configuration And Settings
With root access, you can change system configurations and settings that are inaccessible to regular users. This includes network settings, kernel parameters, and even hardware configurations. Imagine customizing your system to meet your specific needs. But ask yourself, is it always necessary to change these settings? Sometimes, leaving them as they are might be the safest option.
Process Management
Root users can start, stop, or modify any process running on the system. If you’ve ever encountered a stubborn application that refuses to close, root privileges can help you terminate it forcefully. This is particularly useful for troubleshooting and managing system resources effectively. Yet, it’s essential to understand the implications of halting critical processes.
Being a root user in Linux is like having the master key to your system. But remember, with such power, you must tread carefully. Are you ready to take on the responsibility that comes with it?
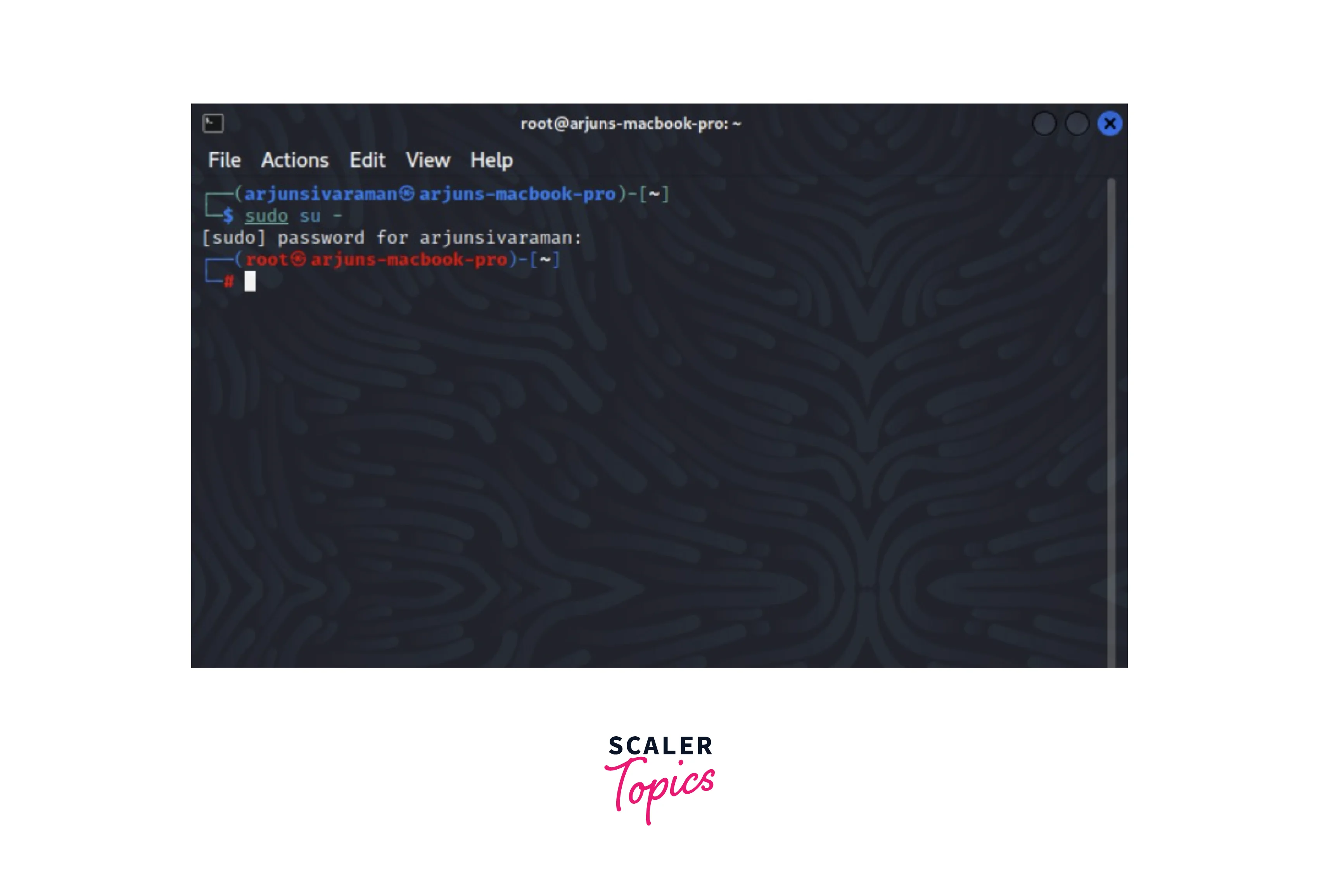
Root User Vs Regular Users
Linux’s root user holds ultimate control over the system, unlike regular users who have limited permissions. Root can access, modify, and delete any file, while regular users operate within confined boundaries. Root privileges should be handled cautiously to avoid system vulnerabilities.
In Linux, the root user is like the king of the system. Regular users have limited power. Understanding this difference is crucial for system management. The root user can access every part of the system. Regular users have restricted access. This section explores the contrast between root and regular users.
Root User
The root user has ultimate control. This account can modify any file. System configurations can be changed by root. The root user can install or remove software. Security settings are under its command. This powerful role demands cautious handling.
Regular Users
Regular users have defined roles. They can access personal files. System files are usually off-limits. Regular users can run programs. But they cannot alter system settings. Their access keeps the system secure. This prevents accidental system changes.
Root access poses security risks. A compromised root user can damage the system. Regular users safeguard critical data. Their limited access minimizes risk. Root user actions must be carefully controlled. Regular users help maintain system integrity.
Managing Permissions
Permissions dictate user access. The root can set permissions for all. Regular users have permissions set by root. Adjusting permissions requires careful planning. This ensures system stability and security. Proper management prevents unauthorized access.
Understanding these differences helps in managing Linux systems effectively.

Credit: www.wikihow.com
Security Implications
The root user in Linux has full control over the system, posing significant security risks. Unauthorized access can lead to data breaches and system corruption. Limiting root access and monitoring activities are crucial for maintaining system integrity.
Understanding the root user in Linux is crucial, especially when it comes to security. The root user holds the highest level of access in a Linux system. With this power, the potential for both productivity and security risks increases.
Access to the root account can lead to serious vulnerabilities if not managed carefully. Let’s explore the security implications of using the root user in Linux.
###
Unrestricted Access
The root user can access and modify all files and commands. This means any mistake or malicious action can impact the entire system. For example, accidentally deleting a critical system file could render your system inoperable.
###
Risk Of Unauthorized Access
If someone gains access to your root account, they can do anything. This includes stealing data, installing malicious software, or even erasing your system. How secure is your root password? It’s essential to use a strong, unique password to protect your system.
###
Accidental Misconfiguration
When working as root, even a simple typo can lead to disastrous consequences. Imagine intending to remove a single file but accidentally deleting an entire directory. To mitigate such risks, consider using a standard user account for everyday tasks.
###
Best Practices For Root Usage
Use root access sparingly and only when absolutely necessary. Implement a policy of least privilege and use tools like sudo to perform tasks that require elevated permissions. This way, you maintain control and minimize potential damage.
###
Monitoring And Logging
Keep track of who accesses the root account and when. Use logs to monitor root activity and quickly identify suspicious actions. What steps are you taking to ensure your logs are secure and regularly reviewed?
By understanding and addressing these security implications, you can better protect your Linux system from potential threats. Remember, with great power comes great responsibility. How will you manage the root user on your system to ensure security without compromising functionality?
Managing Root Access
Root user in Linux holds the highest privilege level. It can access and modify all system files. Managing root access is crucial to maintain system security and functionality.
Managing root access in Linux is a critical task that ensures the security and stability of your system. The root user has the highest level of access, capable of making system-wide changes. This power requires careful management to prevent accidental damage or unauthorized access. Handling root access properly can be the difference between a smoothly running system and a potential security breach.
Best Practices
When managing root access, it’s important to follow best practices to safeguard your system. First, always use the root account sparingly. Regular tasks should be done with a standard user account to minimize risk.
Second, consider using the sudo command, which allows specific users to perform root-level tasks without logging in as root. This creates a clear audit trail, letting you see who did what and when. Third, regularly update and patch your system. This reduces vulnerabilities that could be exploited if root access is compromised.
Tools For Monitoring
Monitoring root access is essential to maintaining system security. There are several tools available that can help you keep an eye on root activities. One popular tool is Auditd, which provides detailed logs of user activities, including root access attempts.
Another tool, Tripwire, monitors changes to your system files and alerts you to any unauthorized modifications. This can be crucial in detecting potential security breaches. Logwatch is another useful tool that generates a daily report of system activities, summarizing critical events and root access logs.
These tools not only help in maintaining security but also provide peace of mind knowing that you can track and respond to any suspicious activity. With these resources, you can manage root access effectively and ensure your Linux system remains secure and efficient.
Have you considered how you manage root access in your Linux environment? What steps can you take today to enhance your system’s security?
Alternatives To Root Access
The root user in Linux holds the highest level of access, with authority over all files and commands. Alternatives to root access include using sudo or creating restricted user accounts. These methods provide control while maintaining security, limiting potential risks associated with full root privileges.
Navigating Linux can feel like unlocking a new world, especially when dealing with root access. Many users equate power with logging in as the root user, but is it always necessary? Let’s explore some alternatives that offer both security and control, without the risks tied to root access.
Using Sudo
Imagine needing full access to your home, but you want to ensure no one can move furniture around without permission. This is where sudo shines. It allows users to execute commands with superuser privileges without needing to log in as root. By typing sudo before a command, you temporarily gain elevated access, making it an excellent tool for everyday tasks that require admin rights.
Using sudo protects your system from accidental errors. I remember a time when a simple typo while logged in as root almost wiped important files. With sudo, such mistakes are less likely to be catastrophic. You can safeguard your system from unnecessary risks while still getting tasks done effectively.
Principle Of Least Privilege
Consider the saying, “With great power comes great responsibility.” The principle of least privilege is the embodiment of this idea in the digital world. It means giving users the minimum level of access—or permissions—they need to perform their jobs.
This approach not only enhances security but also streamlines operations. By limiting access, you reduce the risk of unintended actions or security breaches. How often have you wished for more security in your digital dealings? Implementing least privilege can be your first step toward a safer system.
It’s like having a set of keys where each key opens only a specific door. If someone loses their key, the potential damage is minimized. In Linux, creating specific user roles with distinct permissions ensures that no single user has blanket access to everything.
By opting for these alternatives, you maintain control and security without the risks inherent in using root access. How are you managing access in your Linux environment today?
Common Misconceptions
When diving into the world of Linux, the concept of the “root user” might seem daunting or mysterious. You might have heard whispers that being the root user is akin to wielding ultimate power over your system. While the root user does have extraordinary privileges, several misconceptions often cloud its understanding. Let’s debunk these myths and clarify what it really means to be a root user in Linux.
Misconception #1: Root User Can Do Anything Without Consequence
It’s a common belief that the root user can perform any action without any repercussions. While it’s true that the root user has extensive control, this doesn’t mean actions are free from consequences. Accidentally deleting a crucial file or misconfiguring system settings can lead to significant system issues. Always exercise caution and double-check your commands when operating as root.
Misconception #2: Root User Is Always Necessary
There’s a notion that you need to be the root user for every task. In reality, most day-to-day operations can be completed with regular user privileges. The root user should be reserved for tasks requiring elevated permissions, such as installing software or managing system configurations. Think of it as using the right tool for the job.
Misconception #3: Root User Is The Only Way To Secure Your System
Some believe that using the root user is essential for system security. However, security is more about practices and policies than just user access. Regularly updating software, using firewalls, and following best security practices are key. Over-relying on root access can lead to vulnerabilities if not managed properly. How do you ensure your system remains secure without excessive use of root privileges?
Misconception #4: Root User Is Invulnerable
Another myth is that the root user is invulnerable to attacks. While the root user has extensive control, it is not immune to security breaches. In fact, if compromised, an attacker has full reign over your system. Always keep your root password secure and consider using sudo for tasks requiring temporary root access.
Understanding these misconceptions is crucial for effectively managing your Linux system. By recognizing the limits and responsibilities that come with root access, you can use it wisely and maintain a healthy, secure system environment.
Frequently Asked Questions
What Is A Root User In Linux?
A root user in Linux is the system’s superuser with full administrative privileges. They can access, modify, and delete any file or setting. Root users can install or uninstall software and perform system-wide configurations. This user has unrestricted access to all commands and files.
How To Know Who Is The Root User In Linux?
To identify the root user in Linux, run the command whoami. It returns “root” if you are logged in as the root user. You can also check the user ID with id -u. The root user ID is always 0.
What Is Sudo User And Root User?
A sudo user has elevated privileges to run specific administrative tasks. The root user has full system control, with unrestricted access.
What Is The Difference Between Root User And Normal User In Linux?
The root user in Linux has unrestricted access, while normal users have limited permissions. Root can modify system files and settings. Normal users can only access files and settings they’re permitted to. Root user is crucial for system administration, requiring caution due to its powerful privileges.
Conclusion
Understanding the root user in Linux is crucial. It holds immense power and responsibility. Properly managing root access ensures system security. Always use root privileges cautiously. Mistakes can lead to serious issues. Regular users should avoid using root unless necessary.
Consider using sudo for safer administration. This limits potential damage. Familiarity with the root user enhances your Linux skills. Practice safe and secure computing. Keep learning and exploring Linux features. Your system will thank you. Stay informed and vigilant. This knowledge helps maintain a stable, secure Linux environment.
-

 DevOps6 years ago
DevOps6 years agoSaltstack Tutorial for beginners [2025]
-

 DevOps6 years ago
DevOps6 years agoHow to build a Docker cron job Container easily [2025]
-

 Linux7 years ago
Linux7 years agomail Command in Linux/Unix with 10+ Examples [2025]
-

 DevOps6 years ago
DevOps6 years agoDocker ADD vs COPY vs VOLUME – [2025]
-
 DevOps6 years ago
DevOps6 years agoHow to setup Pritunl VPN on AWS to Access Servers
-

 Linux7 years ago
Linux7 years agoGrep Command In Unix/Linux with 25+ Examples [2025]
-

 Linux7 years ago
Linux7 years agoFind command in Unix/Linux with 30+ Examples [2025]
-
Linux6 years ago
How To setup Django with Postgres, Nginx, and Gunicorn on Ubuntu 20.04

